Tools & Platforms
Major Threat or Just the Next Tech Thing?

Story Highlights
- U.S. adults divided over whether AI poses a novel technology threat
- Majority do foresee AI taking important tasks away from humans
- Most say they will avoid embracing AI as long as possible
WASHINGTON, D.C. — As artificial intelligence transitions from abstraction to reality, U.S. adults are evenly divided on its implications for humankind. Forty-nine percent say AI is “just the latest in a long line of technological advancements that humans will learn to use to improve their lives and society,” while an equal proportion say it is “very different from the technological advancements that came before, and threatens to harm humans and society.”
Despite this split assessment, a clear majority (59%) say AI will reduce the need for humans to perform important or creative tasks, while just 38% believe it will mostly handle mundane tasks, freeing humans to do higher-impact work.
And perhaps reflecting AI’s potential to diminish human contributions, 64% plan to resist using it in their own lives for as long as possible rather than quickly embracing it (35%).
###Embeddable###
Majorities Expect AI to Eclipse the Telephone, Internet in Changing Society
Americans may not be convinced that AI poses a threat to humanity, but majorities foresee it having a bigger impact on society than did several major technological advancements of the past century.
Two-thirds (66%) say AI will surpass robotics in societal influence, and more than half say it will exceed the impact of the internet (56%), the computer (57%) and the smartphone (59%). Just over half (52%) think AI will have more impact than the telephone did when it was introduced.
###Embeddable###
Familiarity Breeds Comfort?
Americans’ perceptions of the impact AI will have on society don’t differ much by gender, age or other characteristics. Most demographic groups are closely split over whether AI is just the next technological thing versus a novel threat. But attitudes vary significantly by people’s exposure to AI.
Seventy-one percent of daily users of generative AI (programs like ChatGPT and Microsoft Copilot that can create new content, such as text, images and music) say AI is just another technological advancement. By contrast, only 35% of those who never use generative AI agree.
This 36-percentage-point gap contrasts with smaller differences between users and nonusers of other AI applications in confidence that AI can be harnessed for good. There is a 27-point difference between users and nonusers of virtual assistants (like Amazon Alexa and Apple Siri) in their view that AI will benefit humans. And there are roughly 20-point differences in this endorsement of AI between users and nonusers of personalized content (such as apps that make movie and product recommendations) and smart devices (like robotic vacuums and fitness trackers).
###Embeddable###
Personalized Content Now Routine; Generative AI Still Novel
ChatGPT reportedly became the fastest-growing app ever, after it was launched publicly in November 2022. However, adoption of generative AI, generally, among U.S. adults is still sparse relative to other types of AI. Less than a third of U.S. adults currently report using generative AI tools either daily or weekly. About a quarter use them less frequently than that, while 41% don’t use them at all.
At the same time, more than four in 10 adults say they use voice recognition/virtual assistants (45%) or smart devices (41%) at least weekly. And nearly two-thirds (65%) report frequent use of personalized content.
###Embeddable###
Demographic Gaps Greatest for Generative AI Adoption
The broad adoption of personalized content is reflected in the relative uniformity of its use across demographic groups. The same is true for virtual assistants and smart devices, except that — possibly reflecting their expense — the use of smart devices is greater among upper- than middle- and lower-income groups and, relatedly, among college-educated and employed adults. Smart devices are also the one technology used more often by women (44%) than men (37%).
On the other hand, there are sizable differences by age, education, employment and gender in the use of generative AI.
- The rate of using generative AI daily or weekly is highest among 18- to 29-year-olds (43%) and lowest among seniors (19%).
- There is an eight-point difference by gender, with more men (36%) than women (28%) using it. However, the gender gap is greater among adults 50 and older than among those 18 to 49.
- Employed adults (37%) are nearly twice as likely as nonworking adults (20%) to be regularly using generative AI.
###Embeddable###
Bottom Line
While Americans are split over whether AI is a routine step in the evolution of technology or a unique threat, most expect it to diminish the need for human creativity and are hesitant to fully adopt it personally. For now, positive views of AI are closely linked with people’s experience with it, rather than their personal demographics. The implication is that as usage expands, acceptance may follow.
Stay up to date with the latest insights by following @Gallup on X and on Instagram.
Learn more about how the Gallup Panel works.
###Embeddable###
Tools & Platforms
Tech giants to pour billions into UK AI. Here’s what we know so far

Microsoft CEO Satya Nadella speaks at Microsoft Build AI Day in Jakarta, Indonesia, on April 30, 2024.
Adek Berry | AFP | Getty Images
LONDON — Microsoft said on Tuesday that it plans to invest $30 billion in artificial intelligence infrastructure in the U.K. by 2028.
The investment includes $15 billion in capital expenditures and $15 billion in its U.K. operations, Microsoft said. The company said the investment would enable it to build the U.K.’s “largest supercomputer,” with more than 23,000 advanced graphics processing units, in partnership with Nscale, a British cloud computing firm.
The spending commitment comes as President Donald Trump embarks on a state visit to Britain. Trump arrived in the U.K. Tuesday evening and is set to be greeted at Windsor Castle on Wednesday by King Charles and Queen Camilla.
During his visit, all eyes are on U.K. Prime Minister Keir Starmer, who is under pressure to bring stability to the country after the exit of Deputy Prime Minister Angela Rayner over a house tax scandal and a major cabinet reshuffle.
On a call with reporters on Tuesday, Microsoft President Brad Smith said his stance on the U.K. has warmed over the years. He previously criticized the country over its attempt in 2023 to block the tech giant’s $69 billion acquisition of video game developer Activision-Blizzard. The deal was cleared by the U.K.s competition regulator later that year.
“I haven’t always been optimistic every single day about the business climate in the U.K.,” Smith said. However, he added, “I am very encouraged by the steps that the government has taken over the last few years.”
“Just a few years ago, this kind of investment would have been inconceivable because of the regulatory climate then and because there just wasn’t the need or demand for this kind of large AI investment,” Smith said.
Starmer and Trump are expected to sign a new deal Wednesday “to unlock investment and collaboration in AI, Quantum, and Nuclear technologies,” the government said in a statement late Tuesday.
Tools & Platforms
Workday previews a dozen AI agents, acquires Sana
After introducing its first AI agents for its HR and financial users last year, Workday returns this year with more prebuilt agents, a data layer for agents to feed analytics systems, and developer tools for custom agents.
The company also said it entered a definitive agreement to acquire Sana, whose AI-based tools enable learning and content creation. Workday said the acquisition will cost $1.1 billion and expects it to close by Jan. 31.
Workday has been on a tear with acquisitions this year. It reached an agreement to buy Paradox, an AI agent builder that automates tasks such as candidate screening, texting and interview scheduling. The deal is expected to close by the end of October. In April, Workday acquired Flowise, an AI agent builder.
HR software, in general, is complex compared with enterprise systems such as CRM, said Josh Bersin, an independent HR technology analyst. Because of that, some HR vendors will have to add agentic AI functionality through acquisition. Workday’s acquisitions this year coincide with the hiring of former SAP S/4HANA and analytics leader Gerrit Kazmaier as its president of product and technology.
“Workday knows that the architecture they have is not going to quickly get them to the world of agents — they can’t build agents fast enough to work across the proprietary workflow system that they have,” Bersin said. “Their direct competitors, SAP and Oracle, are all in the same boat.”
Agents, tools to come
Workday previewed several agents to automate HR work, including the Business Process Copilot Agent, which configures Workday for individual user tasks; Document Intelligence for Contingent Labor Agent, which manages scope of work processes and aligns contracts; Employee Sentiment Agent, which analyzes employee feedback; Job Architecture Agent, which automates job creation, titles and management; and Performance Agent, which surveys data across Workday and assembles it for performance reviews.
Another tool, Case Agent, can potentially be a significant time-saver for HR workers, said Peter Bailis, chief technology officer at Workday. He is a former Google AI for cloud analytics executive who also recently joined the company.
“One of the biggest challenges in HR [is when] an employee has a critical question,” Bailis said. “But their questions are often complex, and processing times for HR departments are often long.”
The case agent can review similar cases in HR, apply the right regional and compliance context, and draft a tailored response for humans to review and deliver.
“The most important part — caring for employees — stays human,” Bailis said.
On the financials side, Workday previewed Cost & Profitability Agent, which enables users to define allocation rules with natural language to derive insights; Financial Close Agent, which automates closing processes; and Financial Test Agent, which analyzes financials to detect fraud and enable compliance. For the education vertical, Workday plans to release Student Administration Agent and Academic Requirements Agent.
Workday also plans agents that bring the functionality of recent acquisitions Paradox and Flowise to its platform.
Expected in the next platform update is the zero-copy Workday Data Cloud, which brings together Workday data with other operational systems such as sales and risk management for analytics, forecasting and planning. Also in the works is Workday Build, a developer platform that includes no-code features from Flowise that enables the creation of custom agents.
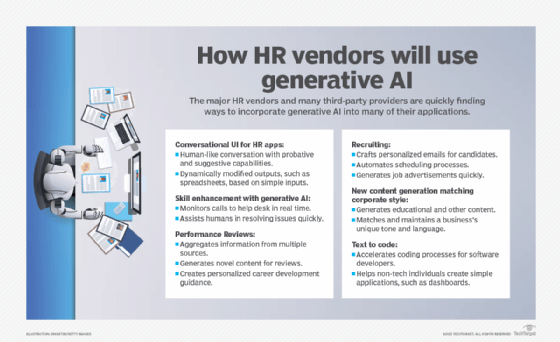
How AI will affect HR jobs
The AI transformation Workday and the rest of the enterprise HR software market is undergoing will likely affect the ratios of HR workers to employees for large businesses, Bersin said.
Currently, many companies aim for an industry standard of one HR employee per 100 employees; with AI agents automating many administrative processes, he said he sees the potential for ratios of 1:200, 1:250, or — in the case of one client that Bersin’s company interviewed — possibly 1:400.
As such, automation will enable companies to do more work with smaller HR teams.
“In recruiting, there are sourcers, screeners, interview schedulers, people that do assessment, people that look at pay, people that write job offers, people that create start dates, people that do onboarding,” Bersin said. “Those jobs, maybe a third of them will go away. In learning and development, there’s a new era where a lot of the training content is being generated by AI.”
Workday previewed these features and announced the Sana acquisition in conjunction with its Workday Rising user conference in Las Vegas Sept. 15-18.
Don Fluckinger is a senior news writer for Informa TechTarget. He covers customer experience, digital experience management and end-user computing. Got a tip? Email him.
Tools & Platforms
Humanity’s Best or Worst Invention? – Pacific Index

Artificial Intelligence is everywhere– and professors at Pacific are less than thrilled
Half the world seems to be under the impression that the creation of Artificial Intelligence (a.k.a AI) is the greatest invention since the wheel, while another half seems to worry that AI will roll over humanity and crush it.
For students, though, it especially seems like humanity has struck gold. Why whittle away precious hours doing homework when AI can spit out an entire essay in seconds? (Plus, it can create fun images like the one you see accompanying this article.) It can even make videos that look so real you begin to doubt everything you see. AI is the robot that’s smarter than you, faster than you, and more creative than you—but maybe it’s not as good as some make it seem.
“I think it’s a mistake to think of it as a tool,” voiced Professor Sang-hyoun Pahk. “They are replacing a little bit too much of the thinking that we want to do and want our students to do.” Professor Pahk recently gave a presentation to Pacific’s faculty on the topic, along with professors Aimee Wodda, Dana Mirsalis, and Rick Jobs. Like many universities around the world, AI has become an increasingly popular topic at Pacific, with some accepting the technology and others shunning it. Professor Pahk explained that there are a lot of opportunities for faculty to learn techniques for using AI as a tool in the classroom, but that not all faculty have a desire to go down that road. “There’s less…kind of strategies for what you do when you don’t want to use it,” he shared, firmly expressing that it’s something he wishes to stay far away from. “It’s part of what we were trying to start when we presented.”
Professor Pahk and his colleagues presented a mere week before school was back in-session, so there was little time for faculty to change their syllabi as a way to safe-guard students from using AI on coursework. Still, many professors seemed to be on a similar page, tweaking their lesson plans and teaching methods to ensure that AI is a technology students can’t even be tempted to use.
“I’ve tried to, if you will, AI proof my classes to a certain degree,” Professor Jules Boykoff shared. “Over the recent years, I’ve changed the assignments quite a bit; one example is I have more in-class examinations.” Professor Boykoff is no stranger to AI and admits that he’s done his fair share of testing out the technology. Still, the cons seem to greatly outweigh the pros, especially when it comes to education. “I’m a big fan of students being able to write with clarity and confidence and I’m concerned that overall, AI provides an incentive to not work as hard at writing with clarity and confidence.” Professor Boykoff, like many of his colleagues, stresses that AI short-circuits one’s ability to learn and develop by doing all the heavy lifting for them.
Philosophy Professor Richard Frohock puts it like this, “It would be like going to the gym and turning on the treadmill, and then just sitting next to it.” Professor Frohock said this with good humor, but his analogy rings true. “Thinking is the actual act of running. It’s hard, sometimes it sucks, we never really want to do it– and it’s not about having five miles on your watch…it’s about that process, that getting to five miles. And using AI is skipping that process, so it’s not actually helping you.” Similar to his colleagues, Professor Frohock doesn’t allow any AI usage in his classes, especially since students are still in the process of developing their minds. “I don’t want it to be us vs the students, and like we’re policing what you guys do,” he admits, explaining that he has no desire to make student learning more difficult, but rather the opposite. “If we want to use AI to expand our mind, first we actually have to have the skills to be thinkers independently without AI.”
This is just one of many reasons that professors warn against using AI, but they’re not naïve to the fact that students will use it, nonetheless. It’s become integrated into all Google searches and social media, which means students interact with AI whether they want to or not. “I have come to the conclusion that it’s counterproductive to try and control in some way student use of AI,” commented Professor Michael Huntsberger. Like other faculty, Professor Huntsberger has adjusted his lesson plans to make using AI more challenging for students, but he recognizes that this may not be foolproof. Still, he warns students to be very cautious when approaching AI and advises, “Don’t use it past your first step–so as a place to start your research…I think that’s a great way to make use of these things, but then tread very carefully.” He suggests that students should leave behind the technology altogether once they’ve established their starting point so that their work can still maintain enough human interaction to be considered student work and not AI.
The problem with any AI usage is that the results that pop up are the product of other people’s work, which encroaches on the grounds of plagiarism. “This is the big fight right now between creators and the big tech companies because the creators are saying ‘you’re drawing on our work,’” explained Professor Huntsberger. “And of course, those creators are, A, not being compensated, and B, are not being recognized in any way, and ultimately it’s stealing their work.”
Pacific’s own Professor Boykoff recognizes that his work is victim of this process, explaining that a generous chunk of his writing has been stolen by this technology. “A big conglomerate designed to make money is stealing my hard-earned labor,” he articulated. “It’s not just me, it’s not just like it’s a personal thing, I’m just saying, as a general principle it’s offensive.”
Alongside those obvious concerns, Professor Pahk adds a few more items to the cons list saying, “Broadly, there’s on the one hand, the social, and environmental, and political costs of artificial intelligence.”
AI 0, Professor Pahk 1.
Looking past all the cons, Professor Pahk acknowledged a bright side to the situation. “It’s just…culturally a less serious problem here,” claimed Professor Pahk, sharing that from his experience, students at Pacific want to learn and aren’t here just to mark off courses on a to-do list. “It’s not that it’s not a problem here, but it’s not the same kind of problem.”
-

 Business3 weeks ago
Business3 weeks agoThe Guardian view on Trump and the Fed: independence is no substitute for accountability | Editorial
-
Tools & Platforms1 month ago
Building Trust in Military AI Starts with Opening the Black Box – War on the Rocks
-

 Ethics & Policy2 months ago
Ethics & Policy2 months agoSDAIA Supports Saudi Arabia’s Leadership in Shaping Global AI Ethics, Policy, and Research – وكالة الأنباء السعودية
-

 Events & Conferences4 months ago
Events & Conferences4 months agoJourney to 1000 models: Scaling Instagram’s recommendation system
-

 Jobs & Careers3 months ago
Jobs & Careers3 months agoMumbai-based Perplexity Alternative Has 60k+ Users Without Funding
-

 Podcasts & Talks2 months ago
Podcasts & Talks2 months agoHappy 4th of July! 🎆 Made with Veo 3 in Gemini
-

 Education3 months ago
Education3 months agoVEX Robotics launches AI-powered classroom robotics system
-

 Education2 months ago
Education2 months agoMacron says UK and France have duty to tackle illegal migration ‘with humanity, solidarity and firmness’ – UK politics live | Politics
-

 Podcasts & Talks2 months ago
Podcasts & Talks2 months agoOpenAI 🤝 @teamganassi
-

 Funding & Business3 months ago
Funding & Business3 months agoKayak and Expedia race to build AI travel agents that turn social posts into itineraries

